Introduction:
If you’re using Azure and looking for a comprehensive solution to generate, manage, and store certificates — whether from integrated CAs, non-integrated CAs, or self-signed certificates — this guide is for you. There’s often some confusion around Azure Key Vault’s capabilities, particularly regarding private key export for certificates, which is a common requirement in certain scenarios. In this tutorial, we’ll walk through a structured approach to clear up these misconceptions and demonstrate a practical setup.
Requirements for this Tutorial:
One Azure Subscription with appropriate permissions (having Owner rights is ideal for testing purposes; in production, provision access thoughtfully).
One Azure Key Vault with RBAC (Role-Based Access Control) enabled, as recommended by Microsoft for managing IAM securely.
All other configuration options area up to you, such as resource access, networking with private endpoint or without.
But for reference I’ll add here a screenshot of what my configuration looks like for ease of implementation
Now let’s start building on top of this:
Permissions required at first glance for certificate management are :
Key Vault Certificates Officer, pasting below the json details in case someone prefers to see here how this would look like.
{
"id": "/providers/Microsoft.Authorization/roleDefinitions/a4417e6f-fecd-4de8-b567-7b0420556985",
"properties": {
"roleName": "Key Vault Certificates Officer",
"description": "Perform any action on the certificates of a key vault, except manage permissions. Only works for key vaults that use the 'Azure role-based access control' permission model.",
"assignableScopes": [
"/"
],
"permissions": [
{
"actions": [
"Microsoft.Authorization/*/read",
"Microsoft.Insights/alertRules/*",
"Microsoft.Resources/deployments/*",
"Microsoft.Resources/subscriptions/resourceGroups/read",
"Microsoft.Support/*",
"Microsoft.KeyVault/checkNameAvailability/read",
"Microsoft.KeyVault/deletedVaults/read",
"Microsoft.KeyVault/locations/*/read",
"Microsoft.KeyVault/vaults/*/read",
"Microsoft.KeyVault/operations/read"
],
"notActions": [],
"dataActions": [
"Microsoft.KeyVault/vaults/certificatecas/*",
"Microsoft.KeyVault/vaults/certificates/*",
"Microsoft.KeyVault/vaults/certificatecontacts/write"
],
"notDataActions": []
}
]
}
}After assigning the above permission we’re moving to generate a self signed certificate just because we are doing a tutorial there will not be a real certificate with an integrated or non-integrated CA, but the process is the same.
Before we hit create let’s stop for a second on the Advanced Policy Configuration, most of the details around this topic are missed by people, this is where the main difference will be, when it comes to export the private key and ensuring a smooth usage/transition from a solution that’s outside of Azure Key Vault to Azure Key Vault.
The most important thing you need to do alongside with configuration that you’d be doing based on your security team’s policy is to ensure you have this option set to YES. This is what ensures that you can export the private key. With this set, we’ll leave everything else to default just because it’s outside of the scope of this particular tutorial, most of these configurations should be coming from your security team as they should define most of the configurations.
Now because this is a self signed certificate there’s not much needed to do, but in other situations here you’d download the CSR , from clicking the cert and clicking “Download CSR”, get it signed and come back and complete the certificate by merging it.
With this part done, let’s click on the certificate until you reach to the below screenshot point:
Here’s the interesting part, although you have the certificate RBAC properly setup, once you click on the “Download In PFX/PEM format” you’re going to get hit by an error such as the below :
In order to fix this you need to do the following, either get a custom role with one specific permission to have the right to Get from the secrets objects, yes basically you need permissions from the Secrets object ( kvs have 3 types of objects : keys/secrets/certificates, and they all have their own set of permissions) but Azure Key Vault will not grant you the entire certificate until you have some secrets permissions, as it treates the private key of the certificate as a secret.
Let’s fix this, by applying the following permission :
Key Vault Secrets Officer
As always i’m adding the Json of this :
{
"id": "/providers/Microsoft.Authorization/roleDefinitions/b86a8fe4-44ce-4948-aee5-eccb2c155cd7",
"properties": {
"roleName": "Key Vault Secrets Officer",
"description": "Perform any action on the secrets of a key vault, except manage permissions. Only works for key vaults that use the 'Azure role-based access control' permission model.",
"assignableScopes": [
"/"
],
"permissions": [
{
"actions": [
"Microsoft.Authorization/*/read",
"Microsoft.Insights/alertRules/*",
"Microsoft.Resources/deployments/*",
"Microsoft.Resources/subscriptions/resourceGroups/read",
"Microsoft.Support/*",
"Microsoft.KeyVault/checkNameAvailability/read",
"Microsoft.KeyVault/deletedVaults/read",
"Microsoft.KeyVault/locations/*/read",
"Microsoft.KeyVault/vaults/*/read",
"Microsoft.KeyVault/operations/read"
],
"notActions": [],
"dataActions": [
"Microsoft.KeyVault/vaults/secrets/*"
],
"notDataActions": []
}
]
}
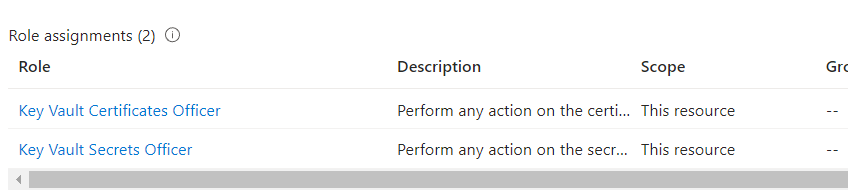
}Now reviewing my permissions on the azure key vault :
As we can now see moving back to the screen where we were before the error :
We can now download the certificate that contains the private key.
From here on, use the documentation found online on how you should break down the pem/pfx certificate such that you can extract the private key.
Final Thoughts:
When implementing solutions found online, always test thoroughly to ensure they’re tailored to your specific needs. Azure Key Vault might not cover every requirement, but it can address many of them effectively. By leveraging available resources like Key Vault, you can streamline essential workflows — in this case, certificate management. From certificate creation and secure storage to automated renewal processes, Key Vault offers robust tools to simplify and strengthen your certificate lifecycle management.